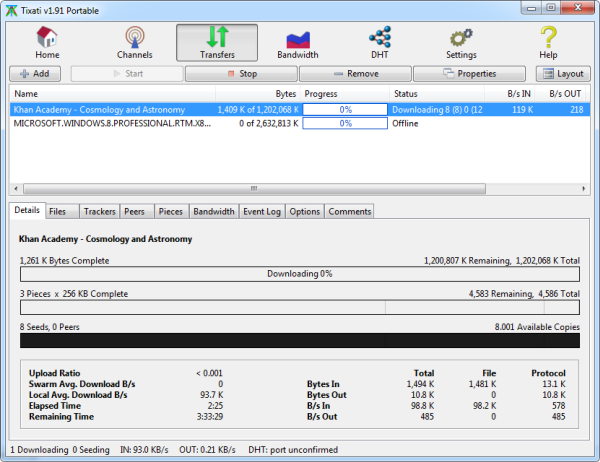
Tixati
Tixati is an easy to use Torrent client with a no-nonsense interface, easily accessible options and vast number of reporting features like detailed peer and swarm information, peer connection encryption, local file management features, scheduled downloads, customizable event logging and more.
Tixati features:
- Detailed views of all aspects of the swarm, including peers, pieces, files, and trackers
- Support for magnet links, so no need to download .torrent files if a simple magnet-link is available
- Super-efficient peer choking/unchoking algorithms ensure the fastest downloads
- Peer connection encryption for added security
- Full DHT (Distributed Hash Table) implementation for trackerless torrents, including detailed message traffic graphs and customizable event logging
- Advanced bandwidth charting of overall traffic and per-transfer traffic, with separate classification of protocol and file bytes, and with separate classification of outbound traffic for trading and seeding
- Highly flexible bandwidth throttling, including trading/seeding proportion adjustment and adjustable priority for individual transfers and peers
- Bitfield graphs that show the completeness of all downloaded files, what pieces other peers have available, and the health of the overall swarm
- Customizable event logging for each download, and individual event logs for all peers within the swarm
- Expert local file management functions which allow you to move files to a different partition even while downloading is still in progress
- Portable version available
qBittorrent
qBittorrent is an easy to use BitTorrent client that comes the closet to what uTorrent has to offer, both in terms of appearance and functionality. qBittorrent is open source and hence supports a wider range of platforms including Windows, Mac OS X, Linux, Solaris, BSD and UNix.
The program includes a built-in search engine with support for major Torrent indexers, RSS feeds, Torrent creator and Bandwidth filtering among other features. It supports all Bittorrent extensions such as DHT, Peer Exchange, Full encryption and Magnet URI. It’s also compatible with UPnP / NAT-PMP and more.
One very useful function of qBittorrent is the ‘alternative global speed limit’ that allows you to toggle between two speed limits with the click of a button. You set two different connection limits, say one with unthrottled speeds and one with limited bandwidth, and then switch one from the other when required. For example, when you want to watch Hulu and also download torrent, you can switch to the low bandwidth mode so that there is enough bandwidth left for stutter free video streaming.
The main features present in qBittorrent are:
- Polished µTorrent-like User Interface
- Well-integrated and extensible search engine
-Simultaneously search well-known BitTorrent search sites
-Per-category-specific search requests (e.g. Books, Music, Movies) - All Bittorrent extensions: DHT, Peer Exchange, Full encryption, Magnet URI, ...
- Remote control through a Web user interface; Nearly identical to the regular UI, all in Ajax
- Advanced control over trackers, peers, and torrents
-Torrents queuing and prioritizing
-Torrent content selection and prioritizing - UPnP / NAT-PMP port forwarding support
- Available in ~25 languages (Unicode support)
- µTorrent spoofing to bypass private trackers white-listing
- Advanced RSS support with download filters (inc. regex)
- Bandwidth scheduler
- IP Filtering (eMule and PeerGuardian compatible)
- IPv6 compliant
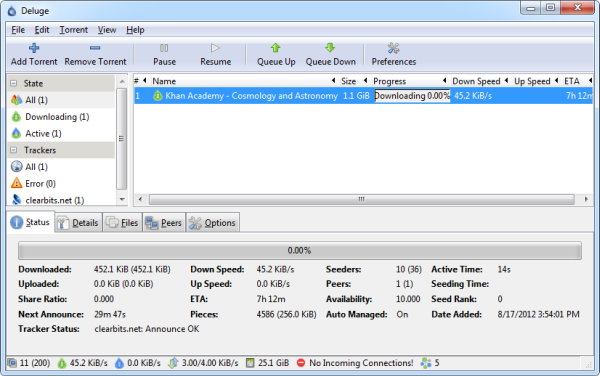
Deluge
Deluge is an open source, and cross platform BitTorrent client that looks just like any other torrent software. The torrents queue is to the top pane, and details on the bottom pane. You can view details such as hash, number of files, comments, tracker, size, download progress and priority of each file. Then there is peers information such as addresses, clients, and there downloading and uploading speed.
In Preferences you can set the default download path, enable the prioritization of first and last pieces of the torrent, use specific ports, enable or disable network extras (e.g. UPnP, LSD, Peer Exchange). You can also set global bandwidth usage, allow remote connections, configure proxy settings, and enable plugins.
Deluge features a rich plugin collection. In fact, most of Deluge's functionality is available in the form of plugins, although you won’t notice these as they are installed by default. A few more are available for download, like Torrent search, RSS feeds, Network Activity Graph, blocklist, scheduler, Growl integration etc.
One option that I like in Deluge, is the ability to minimize the program to the system tray, and password protect the tray icon. There are times when you keep your PC running for torrenting while you are away. You can then put a password in Deluge to prevent anybody from stopping the download or snooping around.





![qbittorent[2] qbittorent[2]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEi0OZ1O7JXSMwuj6aHvT70rEiu0eiiH2PC449CVrAAwEVVn6pDrZ2aBFe8iUy6nUXeGEDz0rbm-JaNpHyFb1OhxwNkI1v4c7SgW7XmnTLrX4sSzR86QecA_9ZzsWijpgiDpkpkKo6F768aN/?imgmax=800)


 Microsoft has released Windows 8 RTM or the final version to
Microsoft has released Windows 8 RTM or the final version to